Why decentralised exchanges are better
In this post, we examine where and why blockchains are presenting unbeatable competition to traditional financial services. As an example. Uniswap DEX offers 20x lower cost to consumers than a traditional finance service.
On phishing, scams and cybersecurity
In the light of OpenSea (alleged) phishing campaign, let's discuss how large is the phishing problem, who should bear responsibility and what can we do to stop phishing?
Estonia and the slippery slope of banning cryptocurrencies
Estonia recently announced its draft updated cryptocurrency legislation. Based on the English translated draft legislation and the Ministry of Finance comments on it, the outlook for cryptocurrency development and decentralised finance startups in Estonia is grim. As was expected: Estonian legislators propose to implement the awaited FATF guidance with no safeguards.
How does your crypto business gets hacked
This week, a prop trading firm mgnr.io lost an eight-figure sum in a classical malicious Microsoft Word attachment hack. In this post, I look at some examples of more serious cyber attacks targetting crypto businesses over the years. These include spearhead phishing, supply chain attacks, and social fraud.
How to money launder Bitcoin
OFAC recently published its sanctions against Suex, a so-called Bitcoin exchange, run by Russians. In the light of these events, this post gives an overview of how Bitcoin money laundering works and how ransomware criminal gangs cash out their proceedings. What are the weak points of regulation and can money laundering be tackled?
How and why Poly network cross-chain bridge lost $600 million dollars
In August 2021, Poly Network lost control of more than $600 million dollar crypto assets to a hacker. The growing community of decentralised finance, or DeFi, users watched the drama develop in horror.
Scaling EVM (Ethereum Virtual Machine)
In this post, we discuss Ethereum Virtual Machine (EVM) scalability and “how fast EVM blockchains can be”. At the moment, EVM powers most of the actively used and popular blockchains. As the popularity of decentralised finance grows, the EVM architecture starts to hit more and more limitations and cannot grow much more. The audience for this post should have a basic understanding of decentralised finance and some of the competing blockchain infrastructure efforts.
The fall of $TITAN: $2B crash of IRON Finance algorithmic stablecoin
How the rise and fall was caused by the greed of the investors themselves. No hacks. Rugged by the people.
How to fix Internal JSON-RPC error on MetaMask and Ledger
Chrome 91 broke Ledger support in MetaMask. Here are instructions for a workaround.
The history and future of cryptocurrencies
How cryptocurrencies developed from 1990 to 2020? How cryptocurrencies will evolve in the future? In this post, I examine the history of cryptocurrencies from technological, cultural and monetary policy perspectives.
The rise of interest-bearing cash
Blockchain has enabled bearer dollars which gain interest in real-time. These tokenised dollars act as interest-bearing cash and will revolutionise finance management.
Ethereum 2.0 staking and staking pool service Stakewise
Ethereum 2.0 staking is launching. In this post, I explore the StakeWise staking pool service, return on investment, risks and technical aspects of staking.
What is the right price for Filecoin and is it worth of mining
This week, after three years of waiting, a decentralised storage project Filecoin launched their mainnet. Filecoin price is in free fall on cryptocurrency exchanges, but still multiple 10x of their ICO price.
Uniswap vs. Sushiswap - the game of decentralised exchange thrones
Last week, a new to-be-launched decentralised exchange called SushiSwap started to make headlines in the cryptocurrency industry. The industry is plagued over the weekend hit-and-run projects, so having a clone project from anonymous authors making a long term impact is unusual. However, this time the trading games named after Japanese cuisine are making a hocket stick blip on cryptocurrency radars.
USDC stablecoin blacklisting and the upcoming storm of crypto justice
TheBlock, a quality cryptocurrency publication, reported this week that USDC, a US Dollar backed stablecoin, has blacklisted one account for the first time in the history. The blacklisted address cannot receive or send USDC funds. Based on EtherScan comment on an associated address, the blacklisted address could be associated with theft.
The explanation for $1,000,000 fee on a single Ethereum transaction
Why somebody transferred $100 worth of ETH with $2,500,000 fee. One fee mistake could be explained by a programming error. But now it has happened more than once, it is likely that it is no longer a mistake.
Cap table service comparison
A short benchmark on different cap table service for international companies. I looked onboarding experience, pricing transparency and international readiness.
A new dawn, a new venture
I am setting up the company website. If you managed to scroll this far down, you have seen all.
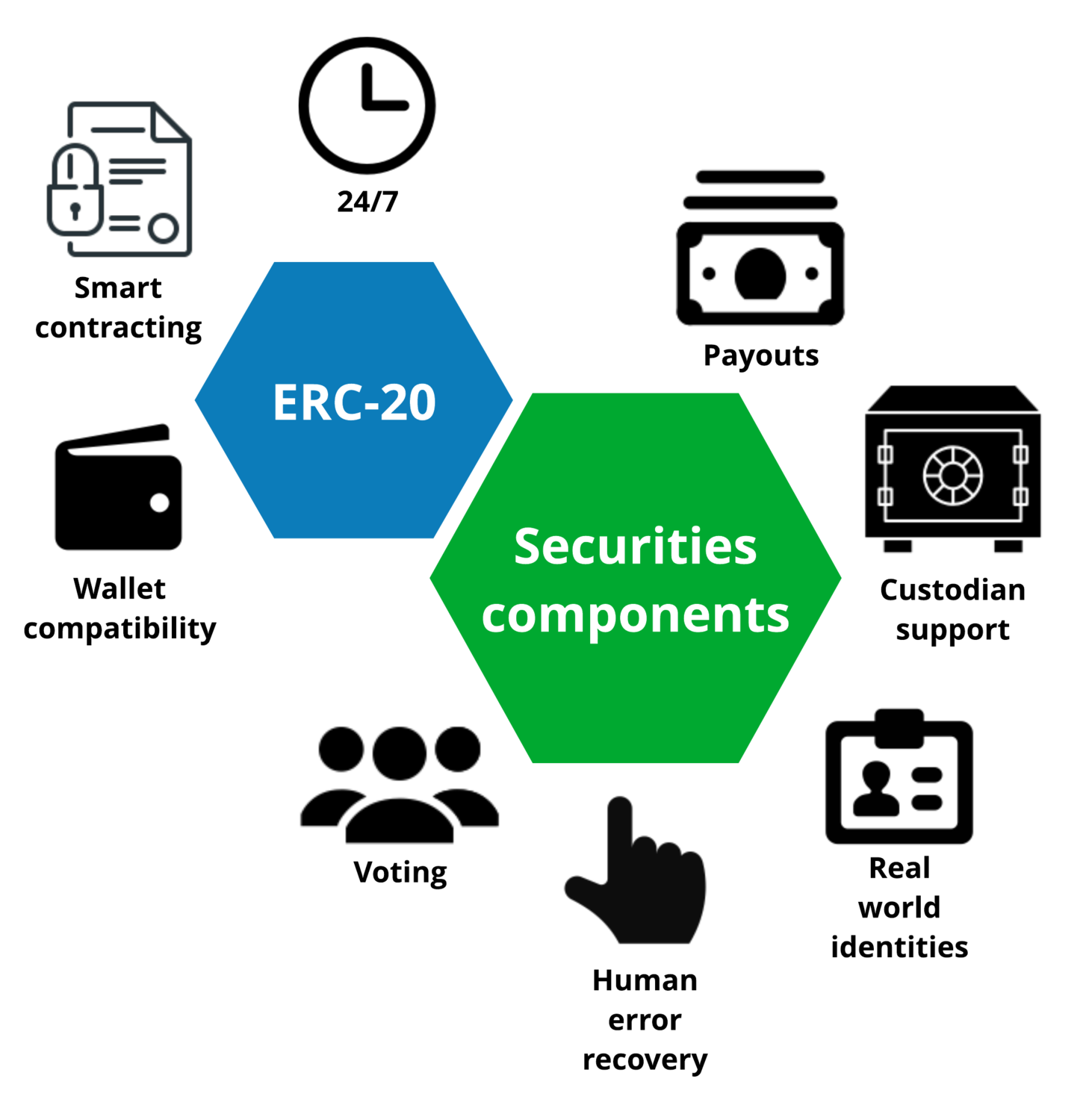
Programming security token smart contracts
How security tokens can run on a public blockchain and still satisfy regulatory requirements
What are securities and security tokens
This article is an introduction to securities and the concept of a security token. Security tokens are a trendy topic in the finance and blockchain communities, as they promise to disrupt how investing is carried out globally. As the security token concept is novel, we hope to clarify it and the surrounding terminology for both technical and finance oriented audiences, professionals and non-professionals alike. The aim of this article is to look at: how security tokens can be defined, how they are different from traditional securities, what kind of tokenised investment deals exist and what regulatory limitations there are.