For discussion, the original thread is available on Twitter.
In the light of the recent event of a prop trading firm losing big monies in an old-fashioned Microsoft Word attachment attack, let me sip my tea and try to remember what kind of hacks I have seen over the years.
👇👇👇
Soon 50 years old MS Office codebase is full of old crappy C code ripe to blow up: macros, buffer overflows, etc.
Open a Microsoft Word document and you are almost guaranteed to have your computer trojaned with RAT (Remote Access Tool).
👇👇👇
The sysadmin of Bitstamp got a GMail conversation where he was lied to receiving an honour (from some university / society). Then he was trojaned with a malicious Microsof Word document.
Bitstamp VPN to the server that has the exchange wallet had two-factor.
The Bitstamp internal investigation post-mortem leaked and is full of good advise, but then it was wiped out from the Internet by Bitstamp legal team. github.com/miohtama/opsec…
Also known as CEO fraud, Business Email Compromise (BEC) or Email Account Compromise (EAC)
👇👇👇
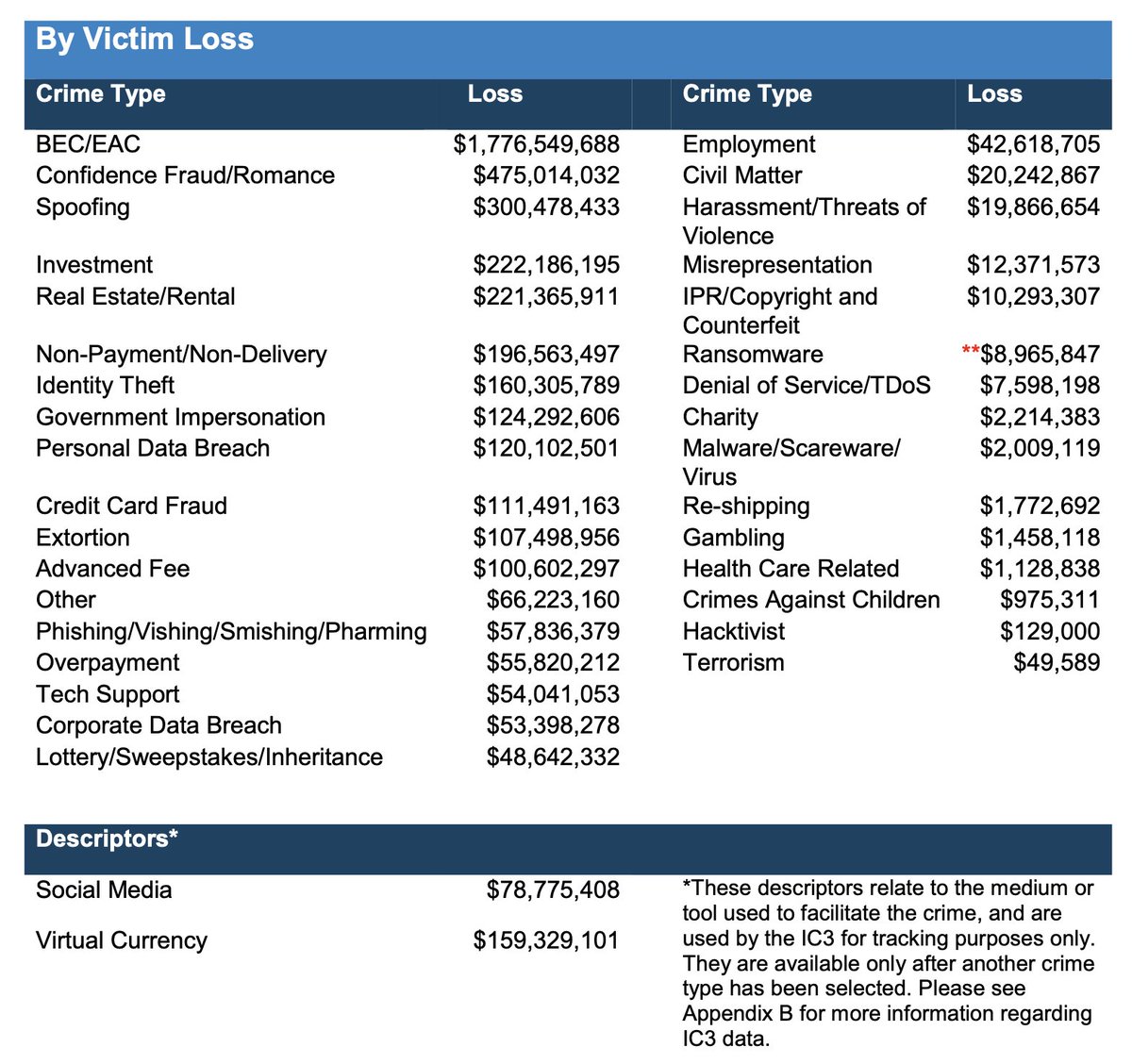 14/ CEO Fraud was in fact the most common form of fraud in the US. See the FBI cybercrime report 2019 (bear market, so the dynamics may have changed).
14/ CEO Fraud was in fact the most common form of fraud in the US. See the FBI cybercrime report 2019 (bear market, so the dynamics may have changed). Train your employees. Don't hire idiots. Don't be an idiot. Have four eyes on every operation so that a single person cannot agree on a high-value transaction alone (multisigs in the case of crypto.)
COMPROMISING SERVER OR SERVICE PROVIDER
👇👇👇
This early Bitcoin developer lost 46,000 bitcoins because of hosting a hot wallet on the @linode Virtual Private Server (VPS) provider.spectrum.ieee.org/thousands-of-b…
Stick with Amazon, Google, Hetzner, the other tier-one providers.
I have personally reset the @Namecheap two-factor authentication by only using the information in emails they sent to me.
As a disclaimer, I advise crypto hedge funds on security. My merits include being at the receiving end of every possible cryptocurrency exchange attack (inc. all of those mentioned above) and losing eight figures of money in multisig wallet hack.

Comments
Send any feedback and comments by replying the Twitter thread.
Discuss